Bug bounties
Taking over Facebook accounts using Free Basics partner portal
There are a couple public examples of Facebook's bug bounty program increasing rewards based on their internal investigation of the report. This is a story of one such report, where a medium-high impact privacy bug turned out to be an account takeover with no user interaction needed.
Initial report: leaking email address of any Facebook user
Sometime late September 2017, one of my websites was approved to participate in the Free Basics project by Facebook and I have gained access to their partners portal. After poking around a bit, I have realised adding a new admin user leaks their address in subsequent notification emails. The bug was quite simple to reproduce (copy-paste from my report):
Using your admin account, go to https://partners.facebook.com/fbs/settings/
Input anything as the name, and in the email field input an email you control.
Click "Add" and intercept the POST request to /mobile/settings/requirements/save/
Change the values[settings.users.userstablecontainer.user_id] GET parameter to an ID of the victim whose email you want to get and forward the request
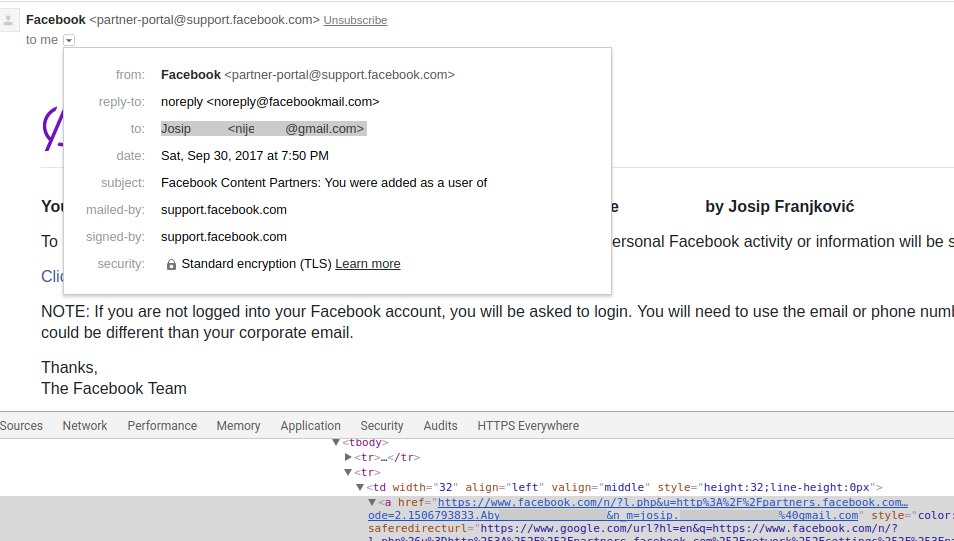
An email will arrive to your controlled address, which will contain the victim's primary mail as part of <a href link >
Basically, I have added a new admin, and set its partner notifications email to one I control. The notification email itself would leak the admin's primary Facebook email through a n_m GET parameter in one of the links.
Screenshot:
Timeline:
-
30th of September, 2017: Report sent
-
2nd of October, 2017: First reply from Facebook's team - triage
-
2nd of October, 2017: Account takeover fixed (note: I did not know about the takeover yet - the full timeline was communicated to me at a later time)
-
24th of October, 2017: Facebook's team has fixed the issue
The email leak issue was not fixed, so I reply telling them the original steps still work.
-
31th of October, 2017: Facebook's team informs me this was actually an account takeover bug, and that the original email leak will be fixed later - it was fixed a couple hours later.
Turns out it was possible to leak login codes somehow. I am pretty sure I have clicked the link itself, and it did not log me in directly. Facebook's team then explained that another parameter from the email link could potentially be used to login to the user's account (with some restrictions) - my test accounts did not have the feature enabled.
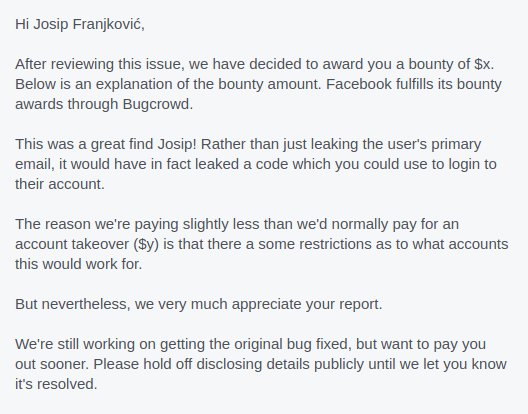
Both of these bugs are fixed.
Thank you Facebook's security team for being (more than) fair - they could have awarded only the email leak bug, and I would never know this was an account takeover.
Random blog post
Bug bounties
